Zero Trust Application Protection for Cloudflare™
The easiest way to verify your application stays secure
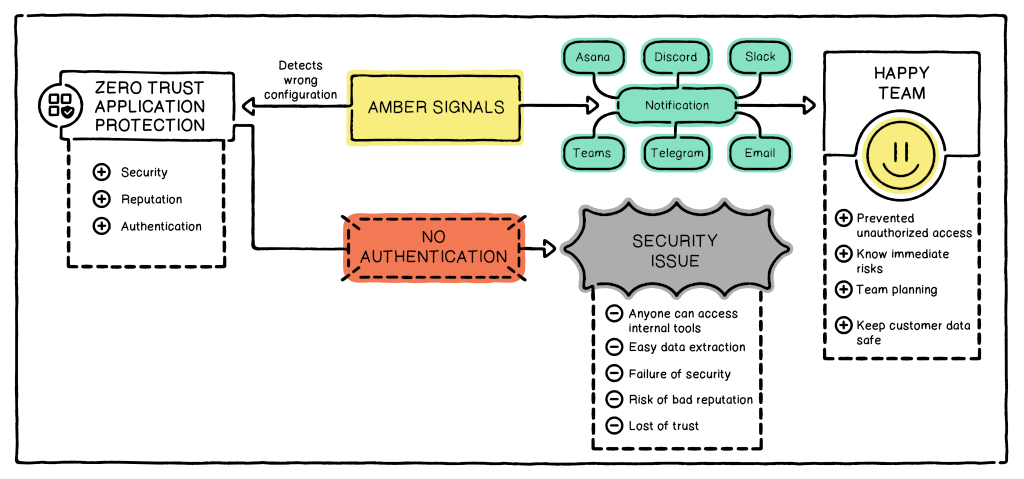
Trust by Verification
Once you've established a Zero Trust Application in Cloudflare, how can you ensure its ongoing security? Accidentally altering configurations is a common occurrence, making it easy to overlook the removal of crucial protection measures.
Consistently ensure the activation of protection
We observe from beyond the protective measures
Receive alerts when the protection is removed


Frequently Asked Question
Our primary commitment is to deliver the utmost security and convenience for our customers
Do you need access to my Cloudflare Account?
No, there's no need for access to your account. By supplying the public endpoint for your Zero Trust Application, we consistently verify the application's protection from outside your network.
How do you verify that the protection is still working?
We monitor the application from an external perspective, enabling us to view it as an attacker would.
How often do you verify the protection?
The frequency largely depends on the service and your preferences. However, as per our standard, we check the status hourly and promptly notify you of any changes.
What happens if the protection is removed?
Upon detecting that an application is no longer protected, we will notify you through the designated channel (e.g., Email or Slack). It is now your responsibility to verify whether the change was intentional or not.
Still have a question about our service?Contact us
Cloudflare, the Cloudflare logo, and Cloudflare Workers are trademarks and/or registered trademarks of Cloudflare, Inc. in the United States and other jurisdictions.